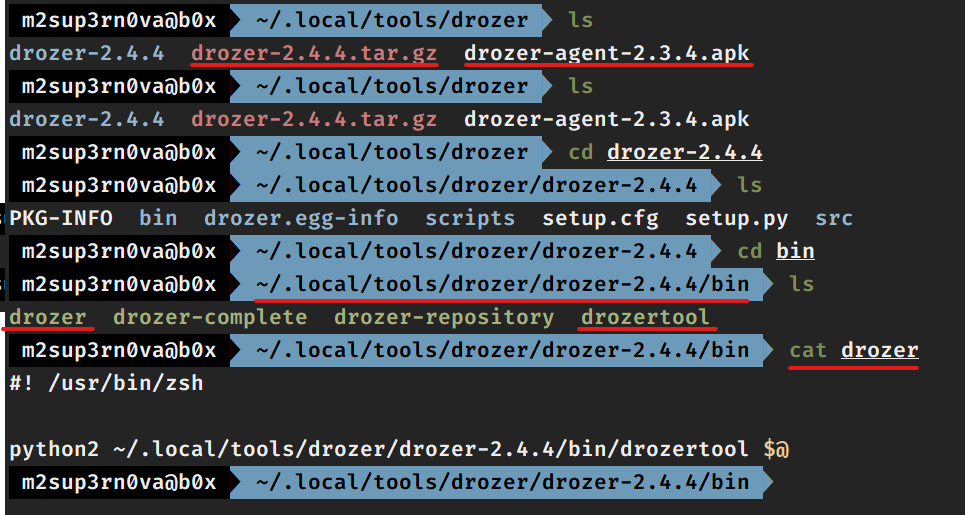
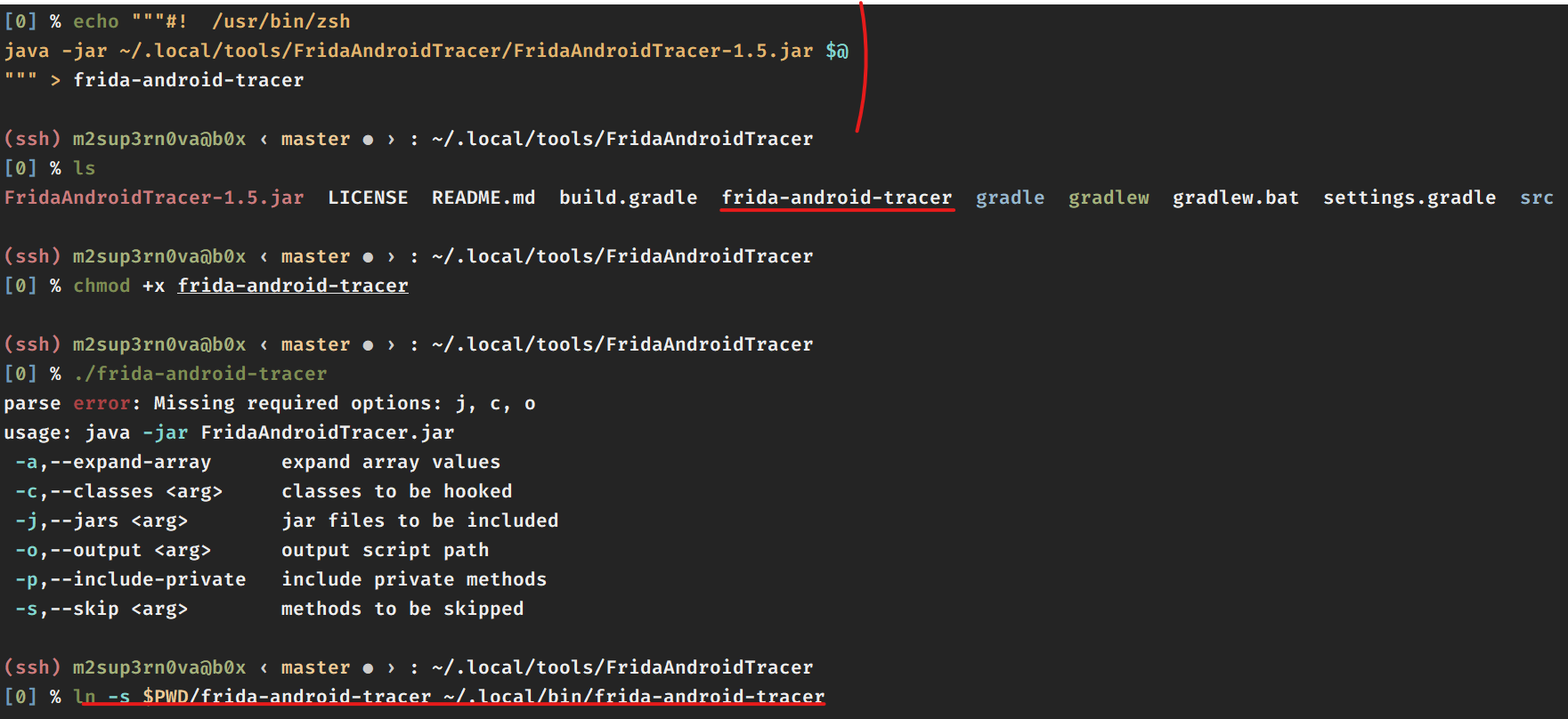
Tool for unpacking APK
Download the latest jar file from : APKTOOL.JAR
Reference : APKTOOL
Create a new folder : mkdir -p ~/.local/tools/apktool and save the jar in this folder
Rename the downloaded jar as apktool.jar
Create a new file called apktool and add lines
#! /bin/bash
java -jar ~/.local/tools/apktool/apktool.jar $@
To create softlink : ln -s $PWD/apktool ~/.local/bin/apktool
Also run : chmod +x $PWD/apktool to make it executable
Now you can run the command apktool from anywhere